Spam or phishing: Why am I getting so many of these messages recently and what should I do with them?
With millions of people teleworking and communicating with each other online during the coronavirus crisis, email has become of the main tools for both professional and personal purposes. Now more than ever before, it is important to learn to detect cyber attacks that come in the form of emails, and follow the recommendations to protect ourselves from them.

Email has largely replaced postal mail when it comes to sending letters, notifications and advertising. It has become a cheaper, and highly common way to contact users for both legitimate and illegitimate purposes. Those engaging in the later have increased their activity during the weeks of the lockdown, and are taking advantage of users’ ‘hyperconnectivity’ to launch their attacks, also over email.
What is spam?
Spam is an email message that is sent to a massive number of recipients for advertising purposes. It is commonly known as ‘junk mail’ as it is of little interest and not requested by the user. That’s why email services tend to automatically filter out these messages and place them in a special folder, similar to mailboxes for advertisements.
These messages could reach users through ‘email marketing’ (campaigns to attract new customers by email) in which their contact information is purchased legally from specialized companies, also known as ‘data brokers’.
A great deal of the spam emails comes from companies with which we have been in contact or had a commercial relationship, and therefore have provided them the information directly.
How is it different from phishing?
gIt is common to find massive phishing in the spam folder - recently they are primarily related to the pandemic or tax returns in Spain. These emails are different from spam in that neither the sender nor their intentions are legitimate. They tend to include fake commercial offers and fake news that include fraudulent contact data and links.
They obtain the email addresses and other information in an unregulated, ilegal market on the ‘dark web’. The information available comes from data leaks and fraudulent offers and surveys on social networks or viral messages on instant messaging apps where users provide their information voluntarily.
Does spam and phishing only take place by email?
No. Although they are the best known, and also used as generic terms for other electronic platforms, there are specific terms depending on the channel. On SMS or instant messaging apps it is called spim instead of spam, and smishing instead of phishing. Finally, vishing is the name for phishing on a telephone call.
Why shouldn’t you open or respond to these messages?
Both ‘spam’ and ‘phishing’ emails are designed to catch users’ attention and get them to open them. Although major email services often prevent ‘malware’ from executing from opening a message, it is important to always:
- Verify the sender before opening any messages.
- Never respond to these messages. If the email is ‘spam’, it tends to come from ‘no reply’ accounts (that are not able to receive messages), and if it is ‘phishing’ you would be confirming that the information they obtained illegally is correct and they can continue using it.
- Do not click on the links, download or open attached documents or trust the contact information in the body of the messages. If you are interested in the offer or want to contact the sender, verify the information on official pages.
- In ‘phishing’ with extorsion, remain calm and do not give in to the criminals’ demands as they are usually generic with made-up information. You should contact the public agency that manages online crime in the country.
Extorsion based on made-up information?
Yes, it’s more common than it may seem. Cybercriminals obtain a batch of emails and send a message in which users are told that the criminals have very sensitive information that could affect their reputation and criminals will make it public if they do not make an urgent payment.
This is the case of ‘sextorsion’, in which the cybercriminal threatens to make public theoretical graphic material and browsing history of a sexual nature. The following example shows how the criminals explain how they obtained the information, what material they will make public if they are not immediately paid in bitcoins and specific instructions of how to do so. It is important to stress that except for the recipient’s email address, there is nothing real in these messages.
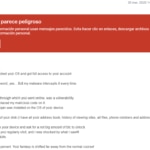
Example of 'sextorsion'
What can you do to avoid receiving ‘spam’ or ‘phishing’?
Although it is difficult to prevent people from sending us these types of emails, there are certain measures to reduce the amount of ‘spam’:
- Provide your email address, contact information or personal data only when strictly necessary and on legitimate pages.
- Do not fill out forms for contact information or surveys to participate in advertiser contests without ensuring that they are legitimate.
- Check the privacy conditions of the companies and platforms with which the information is shared.
- Do not publish sensitive data on personal or professional forums.
- Do not open messages in the ‘spam’ folder without verifying the sender.
- To stop receiving ‘spam’ you must contact the corresponding company to request this. On some occasions they explain how to do so in fine print at the end of the message.
Remember, to protect your email, you are the best defense!
If you want to find out the best ways to protect yourself online during the COVID-19 crisis, read the following articles:
- How to protect the elderly from hackers in the age of COVID-19
- Tips to avoid online misinformation during the coronavirus crisis
- Against coronavirus, you also need to protect yourself online
- The impact of COVID-19 on the spread of cybercrime
- In the age of COVID-19, protect your children on the Internet